Hadi said, “I’m happy now.”
Rini said that she was very tired.
Ita said to me, “Don’t use my car!”
Adi asked me, “What is your name?”
Adi asked me, “Are you sick?”
Ida said to me, “I don’t like you”
What do you want?’ she asked him.
Are you coming with us?’ he asked me.
He asked, ‘When do you intend to make the payment?’
Do you come from China?’ said the prince to the girl.
Answers
Hadi said that he was happy then.
Rini said, “I’m very tired”
Ita told me not to use her car.
Adi asked me, what my name was.
Adi asked me if/whether I was sick.
Ida said to me that she didn’t like me.
She asked him what he wanted.
He asked me if I was coming/going with them.
He enquired when I/he/she intended to make the payment.
The prince asked the girl if she came from China.
RIDHOE
jadilah orng yg brguna untuk orng lain N orng tua..... jgn prnh mnyrh apbla mnghdpi suatu mslh.... kuncinya adlh.....Smngt N trz Smngt
Minggu, 19 Mei 2013
Minggu, 14 April 2013
tugas 2 bahasa inggris bisnis 2
Macam-macam
Pronoun beserta contoh kalimatnya
1.
Demonstrative Pronoun
cth
kalimat:
-
This food is delicious.
-
I love that place.
-
Are you interested to try these cake?
2.
Personal Pronoun
cth
kalimat:
-
He is a politician.
-
It is the most delicious cake that I have ever
eaten.
-
He borrowed me two interesting book.
-
None understands why the man really loves her.
-
If only he shared his problem with me.
3.
Interrogative Pronoun
cth
kalimat:
-
Who moved my stuff?
-
Who is that man?
-
What should I do?
-
Whatever will he do to make me happy?
-
Which did you take?
4.
Relative Pronoun
-
The boy who is playing football on the yard is my neighbour.
-
I looked for the man who borrowed me money.
-
The table which was made of oak wood has broken.
-
He always eats bread whichever he likes.
-
The woman whose car I want to buy is my old friend.
5.
Indefinite Pronoun
-
All have paid the bill
-
This photo is amazing. Do you have another?
-
Is there anybody/anyone who agrees with feminism?
-
Is any safe?
-
If only any are left.
tugas 1 bahasa inggris bisnis 2
Verb+complement+modifier
1.
Ardi is cooking dinner to night
2.
We eat lunch in this restaurant everyday
3.
He saw mom las night
4.
Johny bought a cake tomorrow
5.
He is studying English in her room
6.
He is playing badminton at the park
7.
He ate spaghetti yesterday
8.
She is watering plant in the morning
9.
She is cooking fried rice in the kitchen
10.
The dog is catching the ball at the garden
11.
She bought a dress last yesterday
12.
Dilla bought vcd yesterday
13.
Doni go to stadium at 8 o’clock
14.
They did their homework last night
15.
He is playing football everyday
Selasa, 15 Januari 2013
Sample Memo
TO: English 319 Students
FROM: Rebecca, Fellow Student
DATE: September 17, 2008
SUBJECT: Tips for Working at the Writing Center
Since
our class has yet to perform individual sessions in the writing center,
I have compiled information from a veteran consultant. This
information covers how a typical session might transpire and gives
helpful tips regarding things that may arise during a session. To be an effective consultant, one must first learn how to handle different situations that may appear during a session.
Session Overview
Sessions follow a standard direction, starting with having the student fill out a client needs survey. After
reviewing the students’ needs with them and discussing the paper, you
should have a good idea of what to look for and focus on during the
session. Ask the student to read his or her paper aloud;
if the paper is very long, you may have the student read a section that
they are having the most difficulty with. During the reading, be sure to take notes on and make comments about the mistakes you see or hear. You
will usually be looking for things such as structure, organizational
errors, or the strength of their argument as presented in the paper.
After the student has finished reading, review the notes you have taken with them. Make
sure that the writer understands why you have pinpointed certain
problems and allow them time to ask questions and make changes after
hearing your suggestions. At the end of a session, be sure that the writer is leaving more confident in their writing than when they came in. Thank them for coming into the Writing Center and use the remaining time to fill out the necessary paperwork and emails.
Help
with citations, grammar, and organization are a few main reasons that
people will bring their papers into the Writing Center. Being familiar with some of the basic layouts of citation books will help expedite the process of revision.
E-mails to Professors
Try to keep your e-mail as positive as possible. Make
sure you note the areas that you and the student worked on, so that the
professor has a head’s up on what the student is struggling with. If
a student was very enthusiastic and motivated to make revisions and
better their paper, mention that to the professor as well.
Dealing with Difficulties
· Difficult students
In many sessions you may come across students who have been sent to the writing center for a class. Although it is hard to deal with these students, you should still follow the above steps for a typical session. If they retain nothing else from the session, reading their paper aloud will help them to catch small errors. If
they have nothing that they want to work on and are simply there
because it affects their grade, share your thoughts about their paper
and what to consider revising.
· Helping too much
As a consultant you need to know where to draw the line between helping and doing the students work for them. Easy preventative practices are as follows:
o Never pull the students paper in front of you
o Take notes on a blank sheet of paper instead of on the students paper
o Sit with your writing hand furthest away from the paper
· Offering creative criticism
Make
sure that you word your criticism in a way that the student will see
you are trying to help, not condemning his or her paper. Comment on the positive things as much as the negative. Don’t make your suggestions a personal statement about the writer.
· Being unable to assist
If
you are unable to assist a writer because they are asking a question
pertinent to writing and not about content, ask another consultant or
refer to the reference books. If they ask something
regarding the content of the paper that involves something that they
should be knowledgeable of, then explain that they might need to take
another look at the planning or research stage of the writing process. Remember that you are not there to do the work for the student. If
you find you are unable to help them because of lack of effort on their
part, you should be able to recognize that they need to retrace their
steps and set them in a new direction.
Jumat, 23 November 2012
MY SQL Password Editor
| |||||||
| |||||||
| Fitur | |||||||
| Berikut adalah beberapa fitur khusus MysqlPasswordAuditor | |||||||
| |||||||
| Instalasi & Un-instalasi. | |||||||
| MysqlPasswordAuditor dilengkapi dengan Installer yang dapat membantu Anda dalam instalasi lokal & un-instalasi. Ini memiliki setup wizard intuitif yang memandu Anda melalui serangkaian langkah-langkah dalam penyelesaian instalasi. | |||||||
| Pada setiap titik waktu, Anda dapat menghapus produk dengan menggunakan Uninstaller terletak di lokasi berikut (secara default) | |||||||
| [Windows 32 bit] C: \ Program Files \ SecurityXploded \ MysqlPasswordAuditor [Windows 64 bit] C: \ Program Files (x86) \ SecurityXploded \ MysqlPasswordAuditor | |||||||
| Menggunakan MysqlPasswordAuditor | |||||||
| MyMysqlPasswordAuditor adalah aplikasi GUI yang mudah digunakan, bahkan untuk pemula. Berikut adalah langkah-langkah sederhana | |||||||
| |||||||
| Screenshots | |||||||
| Berikut adalah screenshot dari MysqlPasswordAuditor | |||||||
| Screenshot 1: MysqlPasswordAuditor menunjukkan Password Mysql pulih | |||||||
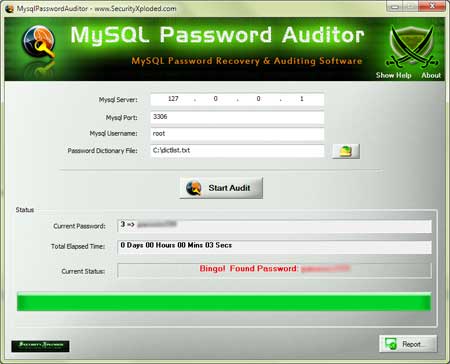 | |||||||
| Screenshot 2: Audit Laporan akhir dalam format HTML yang dihasilkan oleh MysqlPasswordAuditor. | |||||||
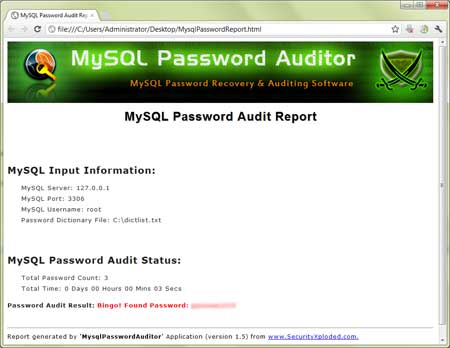 | |||||||
| Rilis Sejarah | |||||||
| |||||||
| Ucapan Terima Kasih | |||||||
| Terima kasih kepada MySql masyarakat untuk kontribusinya terbuka mereka dan membawanya ke ketinggian yang lebih besar hari demi hari. | |||||||
| Unduh | |||||||
|
Ethical Hackers
Ethical Hackers
Ethical hacking adalah tindakan hacking yang dilakukan atas izin dan atas sepengetahuan pemilik. Dengan mengikuti metodologi yang mirip dengan yang penyerang, ethical hacker berusaha untuk melihat jenis informasi publik tentang organisasi tersebut. kebocoran Informasi dapat mengungkapkan rincian penting tentang sebuah organisasi, seperti struktur, aset, dan mekanisme defensif. Setelah ethical hacker mengumpulkan informasi ini, informasi dievaluasi untuk menentukan apakah memiliki resiko potensial atau tidak. Ethical Hacker melakukan probing lebih lanjut untuk menguji untuk setiap kelemahan yang tak terlihat.
Kerahasiaan informasi klien adalah salah satu masalah yang paling dominan dalam panduan ethical hacking. Ketika bekerja pada sebuah proyek, ethical hacker mungkin akan menemukan beberapa informasi penting tentang pengguna atau perusahaan. Ia harus memastikan bahwa informasi ini dirahasiakan. Semua hasil, didokumentasikan serta dalam format elektronik, harus disimpan dalam kondisi yang aman. Informasi dapat berarti banyak pengguna atau perusahaan, dan karenanya ethical hacker menghormati prioritas kliennya
Pengelompokan Hacker
Pengelompokan hacker dilakukan berdasarkan aktifitas yang mereka lakukan, beberapa tipe hacker yaitu :
1. Black Hat Hacker
Merupakan jenis hacker yang menggunakan kemampuan mereka untuk melakukan hal-hal yang bersifat merusak dan melanggar hukum. Kelompok ini lebih tepatnya disebut sebagai cracker.
2. White Hat Hacker
Merupakan jenis hacker yang menggunakan kemampuan mereka untuk menghadapi Black Hat Hacker. Kelompok ini juga dikenal dengan nama security analys, security consultant dan lain-lain.
3. Grey Hat Hacker
merupakan jenis hacker yang memiliki dua keyakinan, kadang mereka menjadi white hat hacker dan kadang pula mereka menjadi black hat hacker.
4. Suicide hacker
Merupakan jenis hacker yang tidak takut pada ancaman hukuman, dan mempunyai tujuan melakukan kekacauan yang sebesar-besarnya. Suicide hacker bisa disejajarkan dengan para teroris bom bunuh diri yang tidak takut mati.
Pengelompokan Jenis Serangan
untuk menguasai komputer korban hacker hanya perlu mengeksploitasi salah satu elemen yang bermasalah pada komputer korban. Elemen atau jenis serangan ini dapat dikelompokkan sebagai berikut :
· Level Sistem Operasi
· Level Aplikasi
· Shrink Wrap Code
· Kesalahan Konfigurasi
Tutorial Ethical Hacking
http://www.youtube.com/watch?v=efMbgI0eeKU
Senin, 19 November 2012
Definition of an Application Letter
Definition
of an Application Letter
An application letter is merely another
name for a cover letter, the official business letter often included with a job
application and/or resume and sent to a prospective employer. Although
application letters are generally considered optional components of applying
for a job, more and more frequently, employers are singling out those who
actually take the time to write an application letter as their top picks. Here
are a few components of a typical, successful application letter:
Professional
Style
Application letters are usually, and
should always, be in an officer letter style, like block style. These letters
should be formatted properly and checked for spelling and grammatical errors.
Salutation
Although many application letters open
with a simple "Sir or Madam:", the more successful application
letters are addressed personally to the hiring manager (which often takes some
research on the part of the job applicant).
Body
The body of a good application letter,
usually 3 to 4 paragraphs, explains why the applicant is a good fit for the
job, explains relevant experience, and shows how that experience would be
useful if selected for the career opportunity.
Attachments
An application letter is rarely sent to
a prospective employer alone. It is usually accompanied by a resume, salary
history, list of references, and/or other documentation of achievements.
Length
Application letters are generally no
more than one page in length. Employers are unimpressed by application letters
of half a page or less, though; filling most of one page is the safest way to
complete an application letter.
Langganan:
Komentar (Atom)
